Analytics, Direct Speech, Internet, Security, Technology
International Internet Magazine. Baltic States news & analytics
Tuesday, 23.04.2024, 23:42
Less than half of companies are prepared to face growing threat from hackers
 Print version
Print version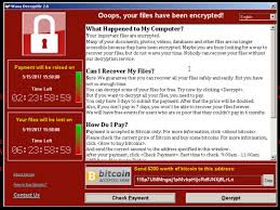 |
|---|
The
hackers are constantly refining their tactics, identifying new ways to extract
money from the businesses and individuals they target. Just a few years ago,
the primary method was phishing attacks that infected the computers of online
banking clients, who were enticed to download malware by clicking on links in
e-mails. After the targets’ computers were infected, the attackers monitored
users’ transactions, stealing their data to authorise fraudulent transactions,
or by using social engineering techniques to trick unwitting clients into
transferring money to the fraudsters’ accounts.
"We've
seen growth in the threat from ransomware for several years," said Eriks
Dobelis, the PwC ITS leader heading its Cyber Security team. After being
installed on a computer, ransomware encrypts files and demands that the user
pay a fee in exchange for decryption. If the fee isn't paid, the user loses
access to the data or it is made public, exposing the user and their
organisation to reputation risk. Large enterprises tend to back up their user
and production data, so the data encrypted by ransomware can be recovered. But
that's not always the case, and backup copies may be at risk if they're
accessible for writing or deleting through the network from an infected
computer. Instead of relying on particular mechanisms such as backup and
antivirus, we need to take a systemic approach to security. Security controls
in a typical Latvian company are quite underdeveloped, and if its basic safeguard
fails, the attacker's further activity may go unnoticed for a long time."
“Recovering
data once it’s been encrypted by ransomware is only half the battle,” said Baiba
Apine, director of the Consulting team in PwC. “The company’s reputation is
also important, and it can be damaged if the stolen information is leaked, or
if information about the incident is revealed. Additionally, the attackers may
install other malware components allowing remote access to the infected IT
infrastructure, not to mention the costs of business interruption due to the
infection, or the need to isolate systems to resolve the problem and reduce the
threat.”
How does the WannaCryptor (WannaCry) ransomware work?
The wave
of infections by the WannaCry ransomware has been building since Friday 12 May.
Many large international companies have been affected by the attack.
As in
the majority of such cases, computers can be infected by e-mails encouraging
users to open attachments, but this attack is distinguished by the
self-propagation mechanism built into the malware, which makes it possible for
the infection to spread itself from a single computer to others in its IT
environment. The malware uses a known hole in Windows that was patched by Microsoft
in its MS17-010 update in March. Unfortunately, software updates and patch
installations take a lot of time in large IT environments, leaving many
computers vulnerable. Additionally, computers with vulnerable Windows systems
can be infected by connecting to public Wi-Fi networks where other computers
are infected. The malware can update itself automatically, installing further
versions that avoid standard detection methods in anti-virus systems.
The
basic rule for this kind of case (if there is no threat to human life) is not
to enter a dialogue with the attackers, and not to pay any ransom.
To limit
the threat of infection and the operation of the WannaCry malware, it’s
important to consider the following actions:
- Immediate isolation of infected workstations
from the remaining components of the enterprise’s IT infrastructure.
- Limiting the ability of infrastructure
components to communicate with the Internet using the SMB protocol, used
for transferring and sharing files (blocking public Internet communication
to and from ports 137, 139 and 445).
- Limiting the ability to use the SMBv1 version
of the file-sharing protocol throughout the entire IT infrastructure.
- Limiting the ability to run unsigned macros in
Microsoft Office documents by changing group policy settings, and allowing
only approved, properly signed macros.
- Ensuring that remote access to IT
infrastructure takes place over a VPN, using Two Factor Authentication.
- Identifying and limiting access by
infrastructure components (without the MS17-010 patch installed) to key
applications and components of the enterprise’s IT infrastructure.
Implementation of the MS17-010 patch on all vulnerable computers in the IT
infrastructure.
- Forced updates of antivirus signatures.
- Ensuring the ability for workstations to
resolve domain names and communicate with the “kill switch” domains used
in the most popular version of the WannaCry malware.
- Monitoring
communication and unblocking resolution for the domains: iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
and ifferfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com).
- Continuously educating and raising awareness
among employees in the area of malware and attack vectors with social
engineering elements.
PricewaterhouseCoopers
Information Technology Services SIA is an IT service provider and part of the
PwC global business advisory network specialising in IT intensive services. PwC
ITS delivers IT solutions, improves cyber security, and helps companies benefit
from big data.








 «The Baltic Course» Is Sold and Stays in Business!
«The Baltic Course» Is Sold and Stays in Business!

